Hello to our nook of the internet! Whether you're here to find inspiration, expand your knowledge, or simply indulge in some great content, you've come to the right place. In this space, we explore a variety of topics that are rich in value but also engaging. From the newest updates to classic wisdom, we strive to offer content that connects with all readers. So relax, unwind, and immerse yourself in the posts that await you!
An effective and cost-effective ways to obtain pictures of Unveiling the Deceptive Nature of Address Spoofing: Unmasking the Illusion of Legitimacy is by searching online. The web is the best tool for get all kinds of information about Unveiling the Deceptive Nature of Address Spoofing: Unmasking the Illusion of Legitimacy.
If you are searching about Unmasking the art of spoofing. a guide to spot and avoid deceptive…, you've visit to the right web. We have 35 images about Unmasking the art of spoofing. a guide to spot and avoid deceptive…, like : Unmasking the legitimacy of timeshare compliance, Prventi, and also Blogs. Read more:
Address Of Scam Corporation: Unveiling A Deceptive Scheme In The World Of Fraud
Unveiling the deceptive nature of biased thinking and illusive perceptions in complex human. Unmasking the cyber tricksters: exposing the menace of email spoofing. Antispoofing: unveiling false source address for network security. Premium ai image. Spoofing cyber broma attacks crime rendering hoax crimen cibernética ataque ip representación. Figure 4 from unmasking illusion of daily-used deepfake applications through landmark focused. Unmasking spoofing: how to detect spoofing in trading. Unmasking ip address spoofing: the cybersecurity threat lurking in the shadows. 145 unmasking the truth: the deceptive nature of alcohol
 kinmagazine.co.uk
kinmagazine.co.uk Github
Top 10 types of spoofing attacks (and how to protect your data). (pdf) unmasking the deceptive nature of cancer stem cells: the role of cd133 in revealing their. Figure 1 from unmasking the deceptive nature of cancer stem cells: the role of cd133 in. Figure 4 from unmasking illusion of daily-used deepfake applications through landmark focused. Antispoofing: unveiling false source address for network security. Email spoofing: unmasking the deceptive cyber threat. Internet protocol spoofing presentation ppt. Figure 3 from unmasking illusion of daily-used deepfake applications through landmark focused. Unmasking ip address spoofing: the cybersecurity threat lurking in the shadows
Author Ibn_shaak Publishes New Book: "unveiling The Deceptive Nature Of Music Addiction In Islam
Unmasking the art of spoofing. a guide to spot and avoid deceptive…. Table i from unmasking illusion of daily-used deepfake applications through landmark focused. Unmasking the legitimacy of timeshare compliance. Internet protocol spoofing presentation ppt. Top 10 types of spoofing attacks (and how to protect your data). Figure 4 from unmasking illusion of daily-used deepfake applications through landmark focused. Unmasking ip address spoofing: the cybersecurity threat lurking in the shadows. Author ibn_shaak publishes new book: "unveiling the deceptive nature of music addiction in islam. Figure 4 from unmasking the deceptive nature of cancer stem cells: the role of cd133 in
 www.issuewire.com
www.issuewire.com Figure 1 From Unmasking Illusion Of Daily-used Deepfake Applications Through Landmark Focused
Figure 3 from unmasking illusion of daily-used deepfake applications through landmark focused. Unmasking the legitimacy of timeshare compliance. Unmasking ip address spoofing: the cybersecurity threat lurking in the shadows. Email spoofing: unmasking the deceptive cyber threat. Figure 1 from unmasking illusion of daily-used deepfake applications through landmark focused. Figure 5 from unmasking illusion of daily-used deepfake applications through landmark focused. Email spoofing: unmasking the deceptive cyber threat. Figure 1 from unmasking illusion of daily-used deepfake applications through landmark focused. Internet protocol spoofing presentation ppt
 www.semanticscholar.org
www.semanticscholar.org Figure 3 From Unmasking Illusion Of Daily-used Deepfake Applications Through Landmark Focused
Sean kearney on linkedin: email phishing and spoofing. Email marketing plans and transactional email api pricing. Email spoofing: unmasking the deceptive cyber threat. Figure 4 from unmasking illusion of daily-used deepfake applications through landmark focused. Unmasking illusion: the enigma of the con queen of hollywood. Unmasking the legitimacy of timeshare compliance. Figure 3 from unmasking illusion of daily-used deepfake applications through landmark focused. 145 unmasking the truth: the deceptive nature of alcohol. Unmasking ip address spoofing: the cybersecurity threat lurking in the shadows
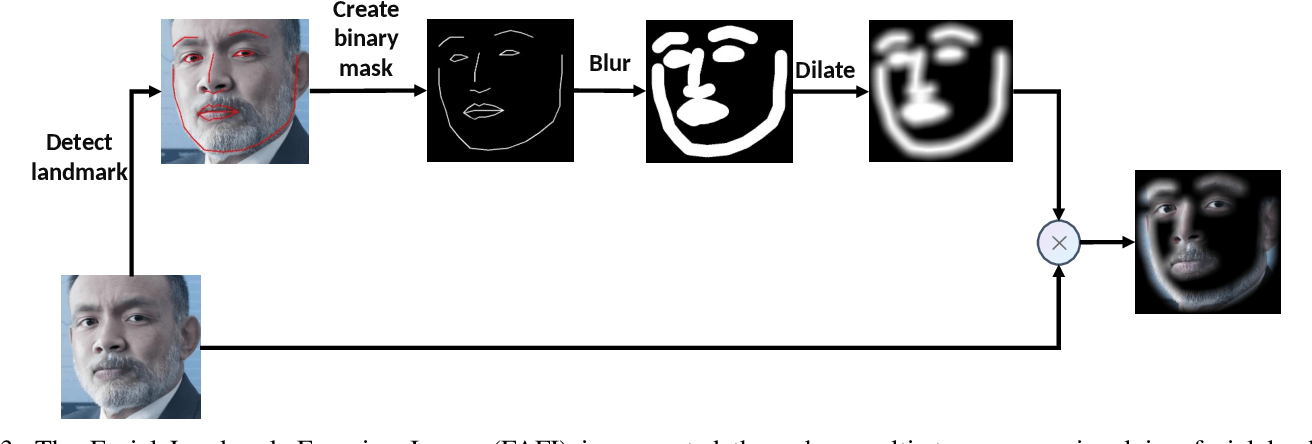 www.semanticscholar.org
www.semanticscholar.org You Might Also Like: 2025 03 Canonprintermx410 25 New Nexus Crossword
Thank you for spending your time to explore this image. We trust what you've found here about Unveiling the Deceptive Nature of Address Spoofing: Unmasking the Illusion of Legitimacy ignites new thoughts and fresh energy. You're always welcome to return whenever you like—ideas are always changing. If you enjoyed this, don't hesitate to share this image and story with your friend. Catch you in the next image!